what to do if you clicked a phishing link
Did you click a suspicious link from an email or text? It's pretty common to accidentally tap a link, with around 40% of emails globally beingness spam and the average American receiving fourteen unsolicited SMS texts per month. Hither'due south what usually happens when you open a phishing link.
Subsequently clicking a phishing link, the sender knows you are a valid target. The assaulter receives some basic data like guess location, device statistics, and any data voluntarily provided. A phishing link may download malware.Users should accept precautionary measures.
Here are some of the most ofttimes asked questions about phishing links. Nosotros've also listed and defined the bottom-known types of phishing. Some have funny yet threatening names.

How do I know if I clicked a phishing link?
If youclicked a phishing link, it's critical to cease interacting with the page and delete any downloaded files. Search for the intended target site using a search engine. Compare the legitimate web address and content to the phishing site. Sentinel for suspicious account activity, calls, or texts.
Follow-on signs of phishing include
- suspicious email messages
- social media posts with shortened links
- copy-cat website URLs
- web pages requiring business relationship login details
- emails with misspellings and unconventional sentences
If the attackers succeeded in collecting data, phishing scam victims might receive manipulative calls or text messages urging them to take further actions. Once a target has responded to a showtime phishing attempt, there'southward a college likelihood they will continue to fall prey to future prompts.
Don't Practise It:
Now's the perfect time to be super suspicious and selective most all your online activities.
Can my smartphone exist hacked past clicking on a phishing link?
A smartphone can exist hacked by clicking a link found in email, text letters, or software. Borer or opening a phishing link tin can expose users to automatically downloaded malware. Sometimes, the malicious link may redirect a user to a malicious website or application controlled by hackers designed to collect user information or infect a mobile phone.
A cybercriminal doesn't demand to go hold of your smartphone to infect it with malware. If your phone is connected to the net, hackers can infiltrate your device through phishing links.
Sometimes, the messages tinseemingly come up from legitimate companies or reputable organizations as a observe virtually their services or apps. Clicking or tapping on these phishing links can open a pathway into your smartphone.
Popular Quiz:
Take a await at this text I received. Study the message advisedly.Tin can yous identify the 5 suspicious parts that should set off alarms? Whorl below for the answers.
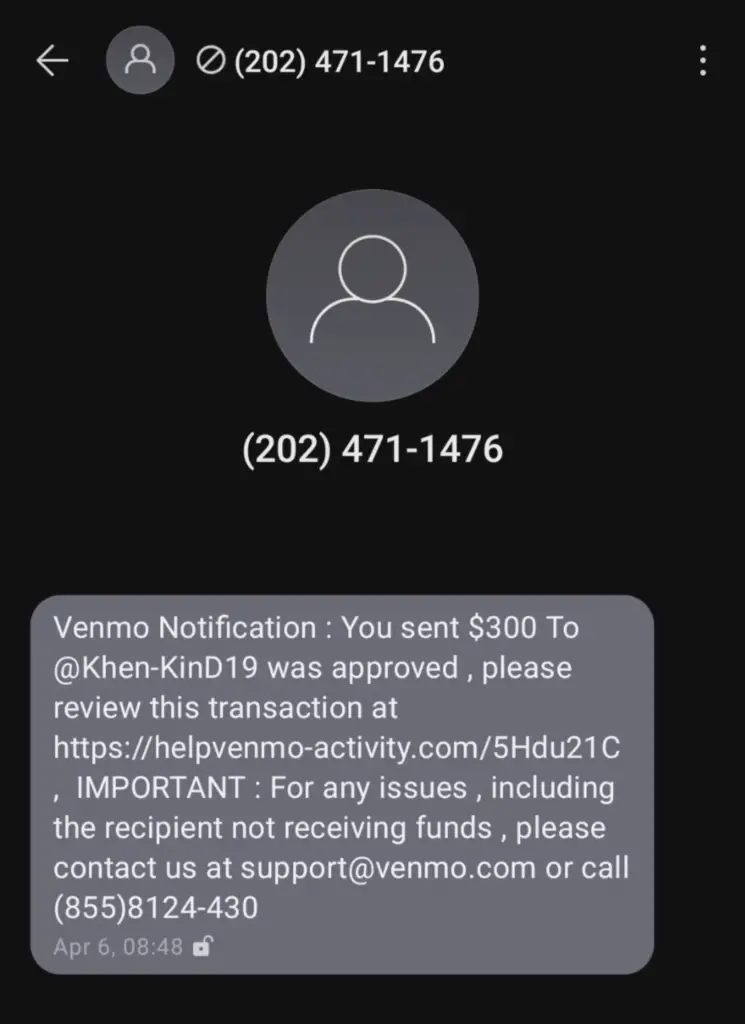
- Claw: Many people would exist worried about losing $300 unexpectedly.
- Curiosity: Nosotros don't know who the user is, but the transaction was canonical.
- Urgency: "Venmo" wants you to review the "transaction" (moving picture me using air quotes) for any problems. The attacker legitimized the message by using the right back up electronic mail and telephone.
- Copy-Cat Link: The link has the discussion Venmo, just it'southward clearly not help.venmo.com (the right URL).
- Bad Formatting: Companies the size of Venmo ensure their notifications are well-formatted.
a. The grammar is incorrect.
b. The toll-costless phone number has the nuance in the wrong place not following the formatting of US or Canadian telephone numbers.
c. There are odd spaces before the commas and colons.
It's also possible that the text bulletin originates from an out-of-service or disconnected telephone number making information technology unwise to call it.

Effects of Phishing Links on Smartphones
Phishing links may exploit smartphones with diverse malware. The attack surface on smartphones is typically smaller. Purpose-built apps can compromise your mobile phone, causing apps to malfunction, ho-hum your device, install unnecessary apps, drain the battery and swallow your information plan faster.
What if I clicked a phishing link on my iPhone?
Investigate where the link redirected the iPhone. Identify the targeted accounts and proactively modify their passwords. Avert disclosing personally identifiable information on any app or service, including your iCloud account. Review your device for unrecognized apps, files, texts, or emails.
iPhones are a bit more protected than Android phones in their susceptibility to malware via phishing links. Clicking a phishing link on an iPhone doesn't immediately expose your sensitive data unless you open whatever website or app. That's why it's critical to stop interaction or action if you've made a mistake.
If your phone is not jailbroken, you're generally rubber from malicious apps. Apple has in-built solid security measures to preclude such incidents.
What if I clicked on a phishing link on my Android phone?
Review where a phishing link redirected your Android phone, noting the site address or any files downloaded. Do not interact with the suspect webpage. Delete any downloaded files. Scan the device for malware using a trusted app. Proactively change the passwords on any targeted account.
Android phones are a bit more susceptible to attacks due to the open nature of the mobile operating system. Since it's possible to side-load new apps or apps from not-official sources, Android users that have riskier usage habits accept the potential to damage their device or accept information stolen from phishing attacks.
What is a phishing link?
A phishing link is a malicious website address designed to steal personal, financial, or business relationship data. Phishing links may initiate malware downloads or browser-based script attacks. Mobile and desktop devices are susceptible to this type of exploit. Users must audit links earlier clicking them.
By the way, some browsers have congenital-in functionality to help baby-sit your privacy. I use and recommend Dauntless as a safer browser with a familiar Chrome experience.
Attackers sometimesmasquerade every bit a legitimate company to entice their target. Once you click on the seemingly genuine link, you'll exist redirected to a malicious website prompting y'all to employ your credentials. Clicking on a phishing link may also install malware into your device to monitor and steal your data.
Phishing links don't just target individuals simplytin exist an attempt to compromise a visitor'southward network and secured data. If an employee clicks on the link, attackers can potentially admission the whole network. It'south all-time to have a piece of work phone dedicated to accessing corporate resources.
What are examples of phishing links?
Examples of phishing links include notifications of new payment, account deactivation, tech support offer, an unpaid invoice, or giveaway winner. By and large, phishing links pb to copy-true cat websites via wait-a-like or shortened URLs attempting to steal account information or download malicious files.
Cybercriminals constantly develop new techniques and methods to execute phishing attacks. These attackers often create urgency, panic, and fear in their victims to manipulate them.
It's crucial to stop and advisedly review a link or requested deportment when at that place's a sense of urgency in the message. Look out for the scarlet flags such equally poor grammar, sense of urgency, asking for personal information, and offers that look too skilful to exist true.

What are the types of phishing?
The types of phishing attacks grow every bit cybercriminals discover new social engineering techniques, communication channels, and types of targets to attack.
Email phishing
Phishing emails are spam or fraudulent emails containing a malicious website phishing URL or attachments with embedded URLs. This is the virtually common advice channel due to the depression toll of launching a campaign. However, spam filters are evolving to include AI and machine learning allowing ameliorate identification and quarantining of suspicious emails.
Vishing
Vishing is a phone call-based phishing set on that entices a target to expose confidential information to cybercriminals via a telephone phone call. Vishing is usually more disarming but requires a highly researched target. Information technology's one of the least used, with only 1% of the phishing attacks attributed to vishing.
Smishing
Smishing is an SMS phishing campaign aimed at stealing personal or corporate confidential data from targets. Smishing victims usually receive deceptive text messages urging them to act urgently, sometimes from spoofed phone numbers.
Spear Phishing
This targeted attack on victims through emails or text containing plausibly authentic information on or around the target to manipulate the victim into activeness. The mark is usually driven more effectively due to the increased legitimacy of the bulletin.
Whaling
Whaling is spear phishing a high-valued target usually carried out against important personnel of a target visitor.
The attackers may impersonate the acme executive to lure a company'southward auditor or IT personnel into obeying specific instructions.
Whaling or CEO fraud is usually aimed at stealing sensitive data, accessing a corporate network, or defrauding the visitor.
Source: https://dataoverhaulers.com/phishing-link-clicked/
0 Response to "what to do if you clicked a phishing link"
Post a Comment